介绍
Rebound 是一台疯狂的 Windows 机器,具有棘手的 Active Directory 环境。通过 “RID cycling”进行的用户枚举揭示了一个 AS-REP-roastable 用户,其 TGT 用于 Kerberoast 另一个具有可破解密码的用户。 ACL 被滥用以获取对 OU 具有完全控制权限的组的访问权限,执行后代对象接管 (DOT),然后对具有 winrm 访问权限的用户进行 ShadowCredentials 攻击。在目标系统上,利用跨会话中继来获取登录用户的 NetNTLMv2 哈希值,一旦破解,就会导致 gMSA 密码被读取。最后,gMSA 帐户允许委派,但无需协议转换。基于资源的约束委派 (RBCD) 用于模拟域控制器,从而启用 DCSync 攻击,从而导致权限完全提升。
收集
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
将域名添加到/etc/hosts文件中;
1 | sudo bash -c "echo '10.10.11.231 rebound.htb dc01.rebound.htb' >> /etc/hosts" |
SMB
空密码可以访问两个文件夹,
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
这两个文件夹皆为空
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
RPC
空密码可以连接
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
NT_STATUS_ACCESS_DENIED 错误表示,由于 权限不足,服务器拒绝了该请求。具体来说,这意味着尝试枚举域用户时,所使用的账户没有足够的权限来执行该操作。
通过rid-cycling-attack手法枚举用户
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
将用户名收集在一个文件中
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
立足
AS-REP-roastting
尝试”AS-REP-roastting”攻击,“不要求Kerberos预身份验证”在”jjones”用户上生效;返回了一个TGT;
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
而然john和hashcat都无法破解出密码
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
Kerberoast
当拿到一个“不要求Kerberos预身份验证”的用户时,可以尝试Kerberoast 不带预身份验证
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
分别返回了krbtgt,DC01$,delegator$和ldap_monitor的ST;破解krbtgt和DC01$的ST不太现实,delegator$一看就是一台机器账户,如果机器账户设置了Laps,想去破解也几乎不太现实;但是”ldap_monitor”似乎是通过”jjones”用户注册的一个ldap服务账户
成功破解出ldap_monitor的密码
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
ldap_monitor:1GR8t@$$4u凭据在SMB其效果,在winrm没有反应(猜测ldap_monitor不在远程管理组中),而且SMB服务枚举一番,并没有收获
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
Password Spray
由于”1GR8t@$$4u”是一个服务账户的密码,尝试密码喷洒,密码在”oorend”用户上同样起效,但是仍然无法通过winrm拿到shell,smb也没有收获
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
滥用ACL
通过bloodhound来查看域内信息
1 | sudo ntpdate -s rebound.htb |
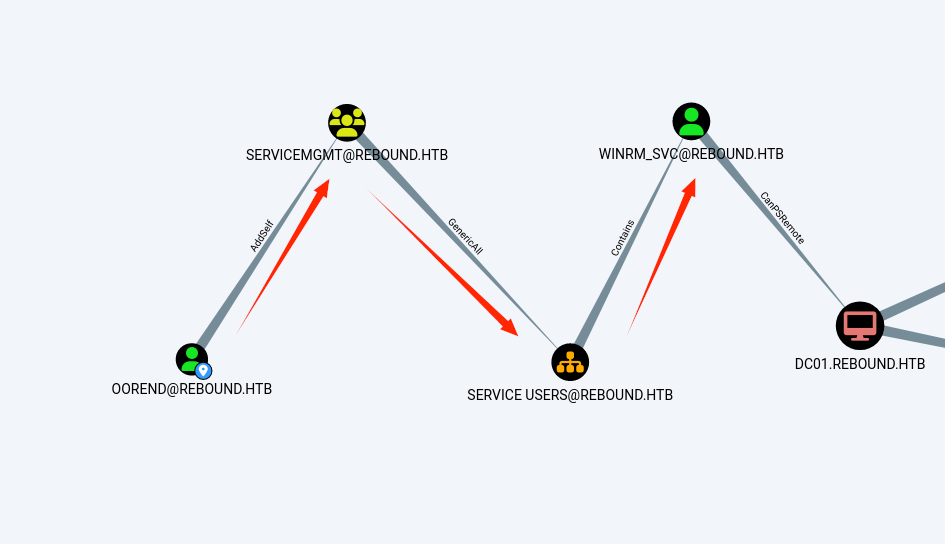
“oorend”对”servicemgmt”组有“self”权限,这意味着,”oorend”可以将自身添加到”servicemgmt”组中;
“servicemgmt”组对”service users”有着”genericall”权限;这意味着,我可以更改或添加”service users”OU的acl
“winrm_svc”在”service users”OU中,这意味着,我可以使得oorend用户对”service users”有完全控制权限,那么oorend就可以去修改”winrm_svc”用户的密码;
脚本如下
1 | #!/bin/bash |
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
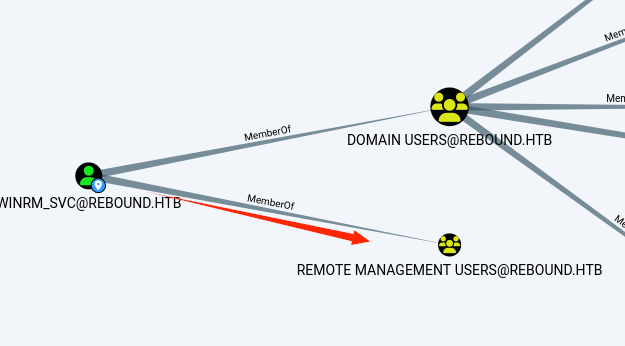
成功修改”winrm_svc”用户的密码之后,我就可以用”LeetPassword123!”密码通过winrm连接,因为”winrm_svc”属于”remote management users”组中,这一点可以在bloodhound中看到;
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
提权
Cross-session
虽然拿下winrm_svc,仍然不能利用”CanPSRemote”到域控机器,因为这个利用手法是需要凭据的,可以从CanPSRemote了解到
正在运行的进程,有一些有趣的事情,session 1 中有一堆进程。通常在 HTB 计算机上,当没有人登录时,我会看到LogonUI和其他几个进程,但这里explorer正在运行,而且看起来有人确实登录了。
1 | *Evil-WinRM* PS C:\Users\winrm_svc\Documents> get-process |
Session ID(会话标识符) 是 Windows 操作系统中为每个用户会话分配的唯一标识符;每个用户在登录时都会分配一个会话 ID,Windows 会区分每个登录用户的会话,并隔离每个用户的进程。0 表示的是 Session 0,通常表示与系统服务相关的进程,因为系统服务通常在会话 0 中运行,而普通用户的交互式进程则在不同的会话中。
qwinsta是显示有关会话主机的信息的命令,但它失败;遇到了这篇 Security Stack Exchange 帖子,它没有解释原因,但表明RunasCs.exe可以使其工作;
1 | *Evil-WinRM* PS C:\Users\winrm_svc\Documents> .\RunasCs.exe oorend '1GR8t@$$4u' -l 9 "qwinsta" |
显示 TBrady 用户已登录;
使用runasCs和KrbRelay的组合,可以强制来自tbrady的连接,这将生成hash。为此,通过-ntlm指定NTLM身份验证,通过-session指定session号,并为具有正确权限的有效RPC服务指定CLSID,从README上列出的默认值中选择
1 | *Evil-WinRM* PS C:\Users\winrm_svc\Documents> .\RunasCs.exe x x -l 9 "C:\Users\winrm_svc\Documents\KrbRelay.exe -session 1 -clsid 0ea79562-d4f6-47ba-b7f2-1e9b06ba16a4 -ntlm" |
成功返回了”tbrady”用户的Net-ntlm hash,尝试用john破解
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
可以成功破解,拿到”tbrady”用户的密码”543BOMBOMBUNmanda”
滥用ACL
在bloodhound中分析”tbrady”用户,发现此用户可以读取一个名为”delegator$”的机器账户的密码
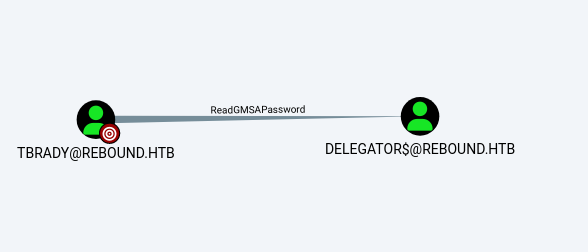
借助”bloodyAD”工具利用”tbrady”的凭据读取”delegator$”的ntlm hash;
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
constrained Without protocol transition
从bloodhound中并不能看到如何从”delegator$”横向移动的路径,但从机器名字来看,不难猜测,这台机器账户和委派相关;
通过’”findDelegation.py”查看域委派相关信息;一看’”delegator$”对域控实现了约束委派
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
不可能用经典的”getST”来滥用约束委派,
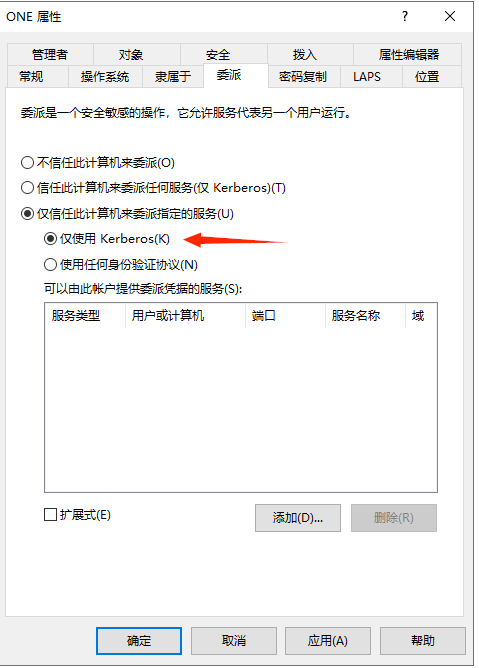
因为此约束委派设置的是”仅使用Kerberos”,这一点可以通过s4u2self申请的ST是否可转发来判断
为了演示这一点,运行getST.py失败:
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
它使用 S4U2Self 为 delegator$ 获取管理员用户的票证,然后尝试使用 S4U2Proxy 转发它,但它失败了(因为ST不可转发);
-self标志告诉getSt.py在 S4U2Self 之后停止,为 delegator$ 获取管理员票证。生成的票证缺少可转发标志:
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
可以看到”Flags”字段中缺少了”forwardable”标志,说明此ST是不可转发的
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
delegations-constrained文章介绍了如何基于约束委派在无协议转换的情况下通过RBCD(基于资源委派)利用;
我的理解:ldap_monitor是一个服务账户;将”delegator$”机器账户的”msDS-AllowedToActOnBehalfOfOtherIdentity”属性修改为”ldap_monitor”的sid,使得ldap_monitor可以模拟DC01$,拿到DC01$到”delegator$”可转发的ST;获得票证后,可以在 delegator$代表模拟用户(DC01$)发出的 S4U2proxy 请求中使用票据,使用此票据,可以获得delegator$委派DC01$的服务的服务票据,以此达到滥用委派的效果
脚本如下:
1 | impacket-getTGT rebound.htb/delegator\$ -hashes :f7f7ea94cd22bd4129ca00bab335ceb9 |
运行结果如下
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
最后将票据提供给secretsdump.py,获得Administrator的hash;使用evil-winrm获得一个administrator shell
1 | ┌──(kali㉿kali)-[~/htb/machines/windows/Rebound] |
