信息搜集
1 | sudo nmap -p- -sT --min-rate 3000 10.10.11.239 |
访问10.10.11.239 codify.htb添加到hosts,发现80端口和3000端口访问页面一样的,还有一个editor路由;
根据index.html,不难看出应该是nodejs的沙箱逃逸
1 | Test your Node.js code easily. |
访问editor路由;存在运行nodejs代码的功能,猜测存在沙箱逃逸
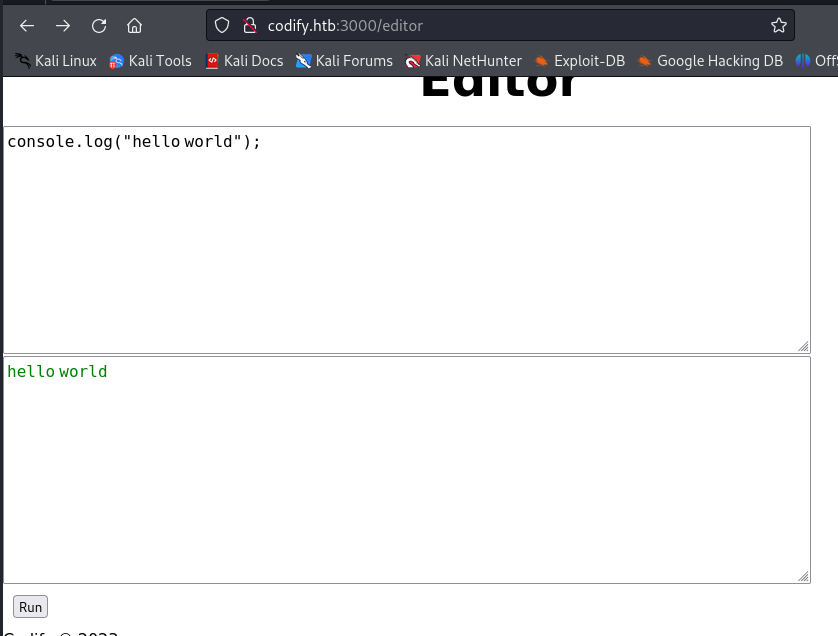
沙箱逃逸
在网上能找到相关poc,但是直接用反弹shell命令一直报错,换一种方式;
1 | ┌──(kali㉿kali)-[~/桌面/Codify] |
nodejs沙箱逃逸这块确实不太懂,以后应该会出一篇博客;poc参考这篇博客clink me
1 | const vm = require('vm'); |
1 | const vm = require('vm'); |
连接到webshell之后,在/var/ww/concat下发现一个db文件,尝试从中得到敏感信息
1 | svc@codify:/var/www/contact$ pwd |
在tickets.db数据库中也是成功发现一个账号密码
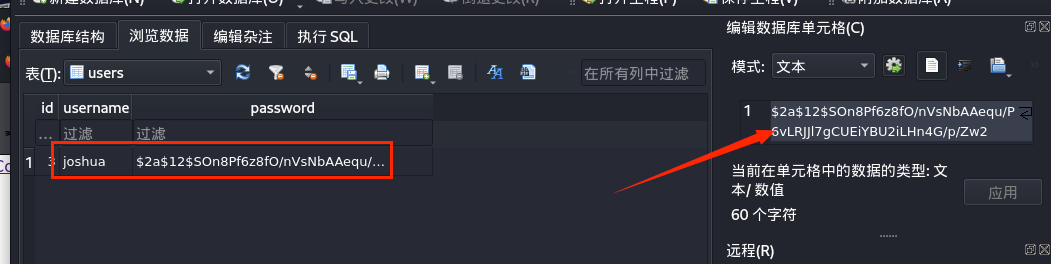
john爆破密码,在尝试ssh连接。是可以成功连接的
1 | john hash --wordlist=/usr/share/wordlists/rockyou.txt |
提权
1 | joshua@codify:~$ sudo -l |
查看/opt/scripts/mysql-backup.sh文件,似乎是一个备份数据库的sh
1 |
|
重点在这,判断输入的密码是否于root密码相同;==判断没有加引号,所以这里并不是字符串比较,这里允许通配符‘* 的存在的,这里的弱比较‘ == ’可以由此绕过,
1 | if [[ $DB_PASS == $USER_PASS ]]; then |
直接用python脚本跑出root的密码,这个脚本也是比较容易理解
1 | import subprocess |
总结
信息搜集到80.3000端口开放,且功能一样;editor路由下存在沙箱逃逸可以实现任意命令执行,反弹shell,得到svc用户,继续搜集在/var/ww/concat/tickets.db文件中可以得到用户名为joshua,用john爆破密码,用ssh连接;发现有(root) /opt/scripts/mysql-backup.sh是一个备份数据库的sh文件,其中存在==判断没加引号,允许通配符‘* 的存在的;写python脚本得到root密码
